Imagine meeting a stranger at a party. You wouldn’t immediately confide your deepest secrets to them, would you? Similarly, when your device connects to a server via TLS, they don’t immediately launch into a secure conversation. Instead, they perform a complex dance, known as the TLS handshake.
TLS is a security protocol that helps establish a secure connection between two parties.
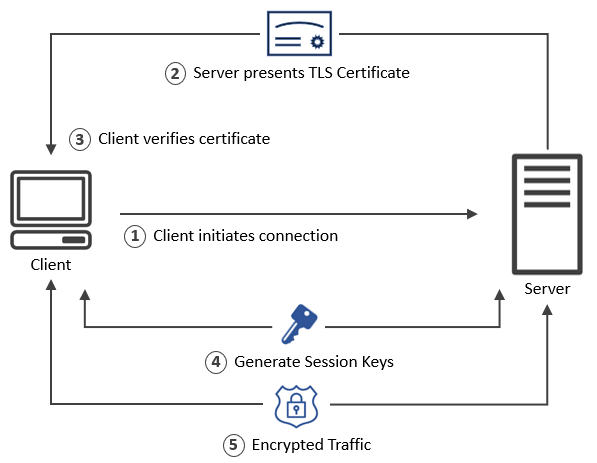
The TLS handshake is a way for two parties to verify each other’s identity and agree on how to encrypt their data.
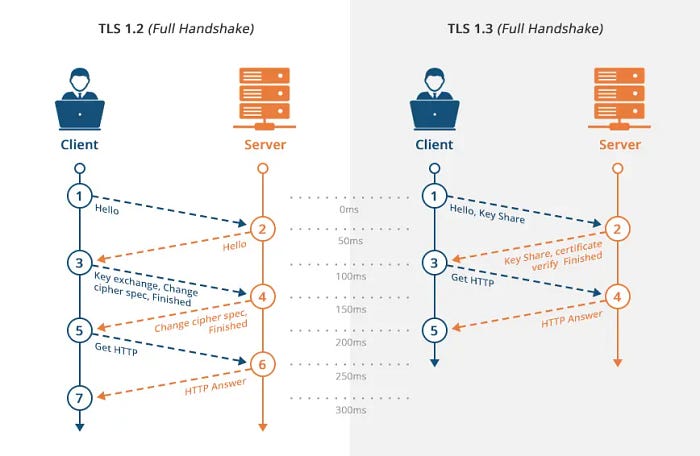
TLS has been updated several times over the years. The current version of TLS is TLS 1.3. TLS 1.3 is a major update to TLS that brings many security and performance improvements.
Now that we’ve covered the basics of TLS, let’s get down to business and talk about the Rustls library.
Rustls library

To establish a secure connection, we’ll use the rustls library.
Rustls is a modern TLS library written in Rust. It is designed to be secure, efficient, and easy to use.
Why Rustls ????
- Security: Rustls is designed with security in mind. It uses modern cryptographic techniques and is constantly being audited for security vulnerabilities.
- Performance: Rustls is very efficient. It is written in Rust, which is a compiled language that is known for its performance.
- Ease of use: Rustls is easy to use. It provides a simple API that makes it easy to implement TLS in your applications.
Let’s code now (I know you just want this)
Here is the code to create a TLS client and server:
use rustls::client::ClientConnection;
use rustls::server::ServerConnection;
fn main() {
// Creating a new client TLS connection to "localhost" on port 443
let mut client_connection = ClientConnection::new("localhost:443").unwrap();
// Creating a new server TLS connection to "localhost" on port 443
let mut server_connection = ServerConnection::new("localhost:443").unwrap();
// Initializing a new TLS handshake with the client connection
let mut handshake = TlsHandshake::new(client_connection);
// Sending a client hello message as part of the TLS handshake
handshake.send_client_hello();
// Receiving a server hello message in response to the client hello
let server_hello = handshake.receive_server_hello();
// Sending a client key exchange message
handshake.send_client_key_exchange();
// Receiving a server key exchange message
let server_key_exchange = handshake.receive_server_key_exchange();
// Sending a client certificate message
handshake.send_client_certificate();
// Receiving a server certificate message
let server_certificate = handshake.receive_server_certificate();
// Sending a client finished message
handshake.send_client_finished();
// Receiving a server finished message
let server_finished = handshake.receive_server_finished();
// Verifying the completed TLS handshake
handshake.verify();
}This code creates a TLS client that connects to the server on port 443. It also creates a TLS server that listens on port 443.
Secure Data
Once the secure connection is established, we can start exchanging data. To do this, we use the send() method to send data over the connection and the recv() method to receive data over the connection.
Here is the code (to add to the previous code) to send a string over the secure connection:
// Send the string "Hello, world!" over the established secure connection
client_connection.send("Hello, world!").unwrap();
// Receive a string over the secure connection from the server
let data = server_connection.recv().unwrap();
// Print the received data
println!("{}", data);- The send() and recv() methods take a string as an argument. The string is encrypted before being sent over the connection and decrypted after it is received.
- The
verify()method checks that the handshake was successful. This ensures that the two parties are who they say they are and that the connection is secure. - The
datavariable will contain the string that was received from the server.
So, after the code. Let’s continue the discution about TLS.
Because is a complex protocol that uses many security techniques to protect communications. Here are some of the other details of TLS:
- Authentication: TLS uses digital certificates to authenticate parties involved in communication. Digital certificates are issued by trusted third parties, such as certification authorities (CA).
- Encryption: TLS uses encryption to protect the data exchanged. The encryption algorithm used depends on the negotiated parameters.
- Integrity: TLS uses a hash function to ensure that the data exchanged has not been tampered with.
- Negotiation: TLS allows the two parties involved in the communication to negotiate the encryption parameters to use. This ensures that the two parties are using the same parameters and that the data is encrypted in a consistent manner.
- Handshaking: TLS uses a handshake process to establish the secure connection. The handshake process allows the two parties to authenticate each other and negotiate the encryption parameters to use.
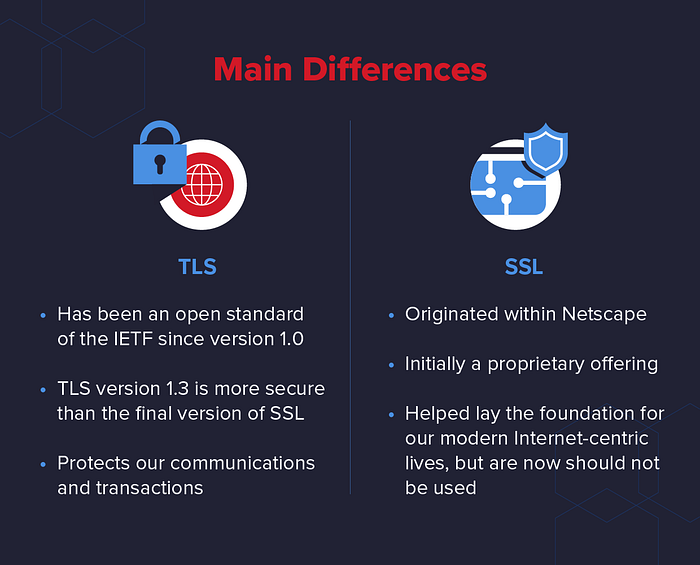
So Why TLS compare to the other protocols. Now its the time to see the main difference with……SSL.
Voila, to finish I will just say. TLS is a critical security protocol that keeps our online world safe and its good to understand little bit about this. Who knows, maybe one day your application will be used by millions of people around the world, and you’ll be able to say that you helped to make the internet a safer place.
